
California Consumer Privacy Act sets new cybersecurity rules: Yea or nay?

Too much red tape, too much control, and too many laws at local, national, and international levels – this is the business world today. However, no regulation is enough when it comes to essentially the most vulnerable industry, i.e. cybersecurity.
On January 1, 2020, the California Consumer Privacy Act (CCPA) went into effect, followed by some amendments effective July 1. It's barely entered into force but already considered one of the strictest laws in terms of privacy protection.
Let's look at how CCPA sets up a new world of cybersecurity compliance, how it differs from GDPR, and what CCPA requirements your organization needs to follow.
What is CCPA regulation?
The CCPA manages the collection, use, and sale of personal data of individual consumers and households in the State of California. The act allows:
- Know what personal information is being collected about consumers
- Ask for the removal of personal information
- Know whether the consumer's personal information is sold or disclosed, and to what third parties
- Say a firm "no" to the selling of personal data
Importantly, personal information under discussion includes all sorts of identifying details (name, residential/IP/email addresses, SSN, passport number, etc.), biometric data, browser and search history, geolocation data, and many more.
Which businesses must adhere to the CCPA?
The CCPA is your go-to act if you collect personal information of individuals based in California, operate there, and meet one of the following criteria:
- Generate $25 million in revenue per year
- Annually handle the personal information of 50,000+ individuals, households, or devices
- Derive more than 50% of annual revenue from selling consumers' personal information
However, everything isn't as Captain Obvious-y as it may seem. For instance, if your website has at least 50,000 California visitors annually, then you must operate under the CCPA, even if you work on the East Coast.
Interesting fact: A recent survey found that 85% of respondents haven't taken sufficient measures to prepare for the CCPA, even though they knew they fell under the corresponding rules. Even worse, many companies simply don't know what types of data they collect or how it's processed.
CCPA vs. GDPR: What is the difference?
Though heavily inspired by the GDPR, the CCPA has a couple of distinguishing features. Most fundamentally, the CCPA omits several specific types of data, such as medical and protected health information.
The CCPA also excludes several specific processes from the definition of "selling," including transferring the personal data to third parties as part of merger, acquisition, or bankruptcy activities.
The GDPR isn't used in the personal or household context, while the CCPA doesn't deal with noncommercial activities. Still, the GDPR only covers individuals, and the CCPA refers to businesses.
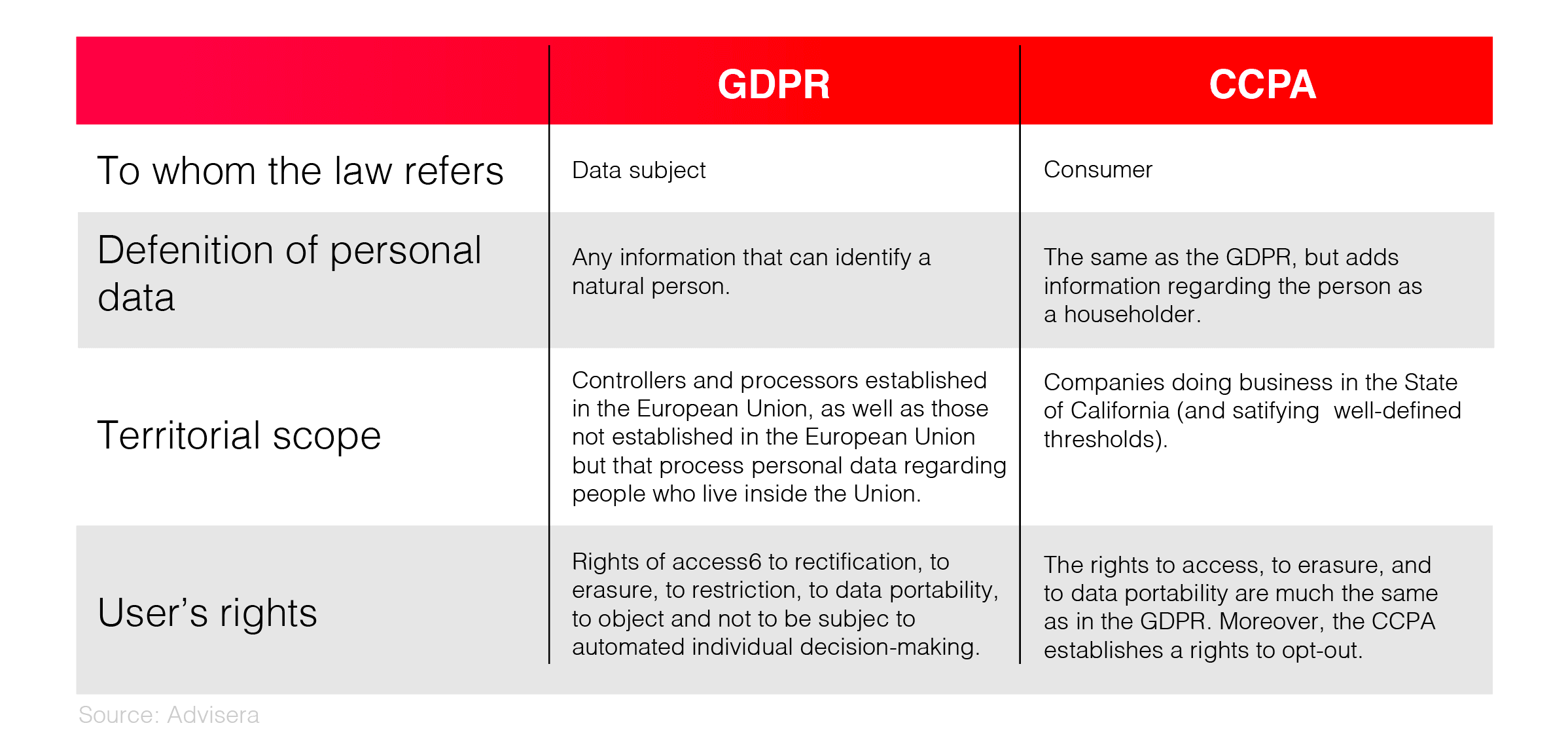
Unlike the CCPA, GDPR also defines specific conditions for how organizations protect the data, prevent cyber incidents, and report breaches.
So, how does the CCPA impact cybersecurity?
The CCPA doesn't specify any direct cybersecurity obligations. In fact, the act only states that companies should follow the rules of reasonable security – what's meant by "reasonable" isn't explained.
Ironically, many more details are available regarding penalties. The CCPA allows consumers to seek statutory damages of between $100 and $750 (depends on the seriousness of mistake, number of breaches, etc,) per incident or record in the event of a data breach.
To stand against civil actions, a company must prove that it has taken serious measures in terms of protection of personal information.
CCPA compliance checklist: Steps companies should take
While there's no clear definition of "reasonable security," the California Department of Justice (DOJ) issued the California Data Breach Report that enlists 20 essential data security controls offered by the Center for Internet Security (CIS Controls). The CIS Controls form the minimum level of security, including:
- Basic controls (control of hardware and software assets; usage of administrative privileges, monitoring, etc.)
- Foundational controls (protection of email and browsers, data recovery, account management, etc.)
- Organizational controls (incident response plan, penetration tests, etc.)
As part of a broader initiative, companies should consider following the NIST (800-53 or CSF) or ISO 27001 standards.
What's more, some extra CCPA compliance requirements are appropriate to protect the personal information the company is processing:
- Conduct data flow mapping exercises to identify what types of personal information are collected. Look through the present security policies and practices to determine potential loopholes and areas for improvement.
- Develop a written information security program (WISP) that would encompass all possible measures you take to avoid data breaches. Also, it should contain rules for employee training, vendor check-ups, risk management, and an incident response plan.
- Perform annual (or better, biannual) audits to make sure you comply with the main WISP provisions. It's highly recommended to involve a law firm to protect the results under attorney-client privilege.
- Draft contractual provisions that would shift liability and risks to third parties. This way, you show your company cares about personal data even when it's processed by other stakeholders.
- Reconsider the way you store personal information. Redacting and encrypting can help you adhere to the CCPA standards as well as defend against statutory damages in a private action.
Is CCPA the future of cybersecurity legislation in the US?
The impact of the CCPA is yet to be observed, but since California is the fifth-largest economy in the world, we're sure the act will have a global impact.
However, two major cybersecurity trends are already underway. First, state governments will follow the example of the Golden State, enforcing certain data privacy and security regulations.
As a result, we'll face a whole variety of legislation not mutually recognized in different states. So, Congress will likely work out a single document similar to the GDPR in the EU.






