
Best practices for DevOps security

DevOps has taken the IT world by storm. The tech community turned to DevOps and microservices in order to develop and implement code faster and more efficiently than older-style cascade projects.
High velocity IT is vital when it comes to staying competitive in the market. In order to survive, businesses have to develop as quickly as possible while delivering innovation at the same time. And let's not forget that one of the most important things everybody has to pay close attention to now is cybersecurity.
When security meets DevOps
DevOps, as the name implies, is bringing development and operations together. But it's more than just that. If you want to make the most of the agility and responsiveness that DevOps offers, IT security must become an integral part of every single stage of the development process.
In theory, the DevOps team responsibilities include maintaining security by design. In practice, however, security is often included later in the product life cycle as an afterthought.
Thus, the idea to build security into the DevOps workflow concept was born. This type of "baked-in" DevOps security led to the rise of a brand-new term called "DevSecOps," which is aimed at enhancing security through increased collaboration and shared responsibility.

Why join the DevSecOps army
Companies that go for DevSecOps benefit in multiple ways.
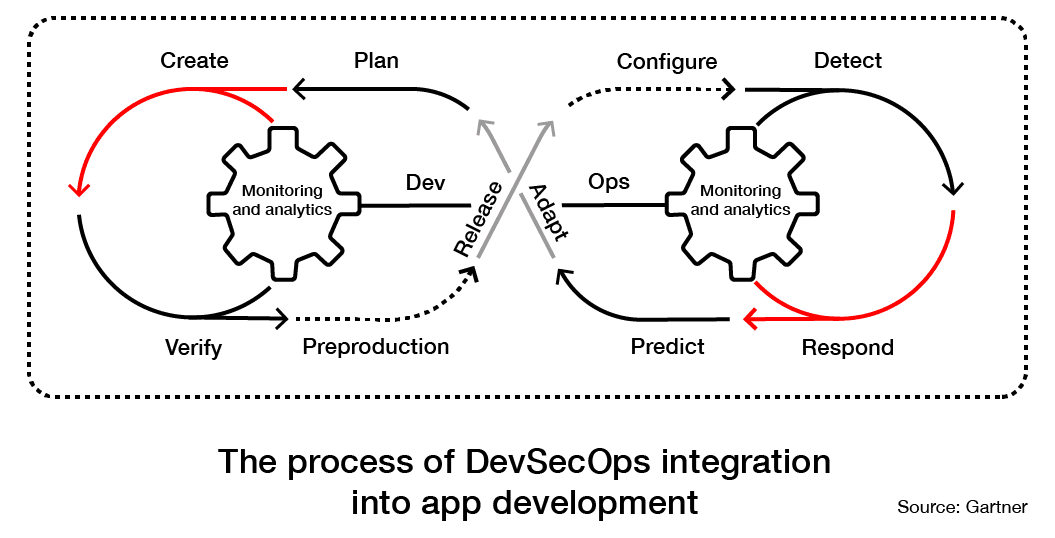
DevSecOps is a robust approach that places each team member in charge of security. It's unacceptable for someone to roll out an application and then just leave it to colleagues to think about security.
This collaborative framework holds a lot of other advantages:
- Detecting and fixing security issues throughout the development workflow increases the speed of delivery and reduces costs.
- There is faster recovery speed in the event of security breaches thanks to templates and pet/cattle methodology.
- Automated testing and processes make tests more coherent and the overall DevOps chain more consistent.
- Effective management and deployment of security auditing, monitoring, and notification systems allow addressing cybercrime "trends".
- DevSecOps fosters a culture of continuous iterative improvements.
- Secure products ensure increased customer value.
DevOps security best practices
Any company should take privacy and security principles seriously and translate them into concrete actions through DevSecOps best practices. As DevOps includes cultural, organizational and technological components, it goes perfectly with security programs that usually include 3 components:
- People
- Processes
- Technologies
Here are the main DevSecOps best practices across these three key pillars.
People and culture
Any successful security program will invest in proper staff training. It is vital to educate teams about practical hacking experiences and vulnerable applications in order to raise awareness of possible risks.
Proper training will promote a corporate culture where security becomes less a function and more a mindset that all team members share.
All of this further contributes to the successful implementation of security technologies as well as ensuring faster, easier and cheaper software delivery cycles.
Processes
Streamlined processes are essential to DevSecOps success. It's necessary to create and implement agreed ways of working that are well-documented and familiar to all. DevSecOps ensures short and feedback-driven security loops that allow to quickly identify problems and respond as fast as possible.
Technologies
Without automated security tools for code analysis, compliance scan, configuration management, patching, and vulnerability management, you will likely fail to scale security of the DevOps processes.
Any case requiring us to upload and process data is subject to errors. Automation leads to fewer risks arising from human mistakes.
Generally, it is necessary to create the DevSecOps cycle where the code is inspected, configurations are checked, credentials are stored safely, and vulnerabilities are detected and eliminated automatically.
Effective DevOps security demands all coding standards be continuously checked against new security recommendations. Code changes should be verified and tested in line with these recommendations as every single change matters.
You can start with the OWASP Top 10. By converting the code changes into QA testing, you can take advantage of the automated testing facility to provide timely feedback to the development teams. Also, the OWASP ASVS with 19 verification domains is adaptable to building secure software.
Additionally, Attack Driven Development enables developers to learn about the tools, techniques, and processes of software development and application security at the same time.
It's crucial to ensure that all devices, tools, and accounts are permanently discovered and validated, and brought under security management according to your policy.
Application-level auditing and scanning are two of the most important parts of DevSecOps that allows business to fully understand their risk posture. Source code scanning, IDE integration, binary scanning, and pre and post-deployment auditing represents a higher degree of security code assurance.
It is also vital to ensure you use privileged access management tools in the DevOps process in order to prevent cases when privileged user rights are escalated or bad code is exploited. This means you should restrict developers' and QA engineers' access to specific development, set up least privilege access rights by default, and consider a regular audit of credentials and access rights in the access management tool.
Segmenting the network reduces the risk of cases when a local breach lets hackers get immediate access to a substantial part or even the whole infrastructure. It is achieved by allowing users to create networks that make communication between containers secure. So, the application layers are basically logical units that don’t trust each other by default. When someone hacks into one segment, they will face the security layers of the other ones.
Wrapping up
In the technology universe, the only constant is change. Outdated security measures can ruin even the most effective DevOps practices. This is why security is at the very core of DevSecOps. It allows IT companies to ensure the safety of business and customer-sensitive data and thus make the development processes more efficient.
DevSecOps is rising in popularity, and only you can decide if it is right for you. Our DevOps consultants always stay up-to-date with the latest DevOps security trends and we can't wait to help you with all your DevSecOps needs!






